Introduction
The Structured Exception Handler (SEH) mechanism enables developers to take actions on unexpected events during the execution of a thread. The SEH mechanism is implemented within Windows operating system and the developers can leverage it by using _try/_catch code within their applications. In this article, I’ll go through the basics of SEH overflow to help others with their exploit development journey.
Exception_Registration_Record
The Thread Environment Block (TEB) structure has a pointer named ExceptionList which points to the structure _Exception_Registration_Record. The _Exception_Registration_Record structure is extremely important for SEH overflow since it contains two pointers Next and Handler which will be overwritten during exploit development process. Here is an overview of accessing TEB and _Exception_Registration_Record inside WinDBG.
-
Getting
ExceptionListpointer inside ofTEB.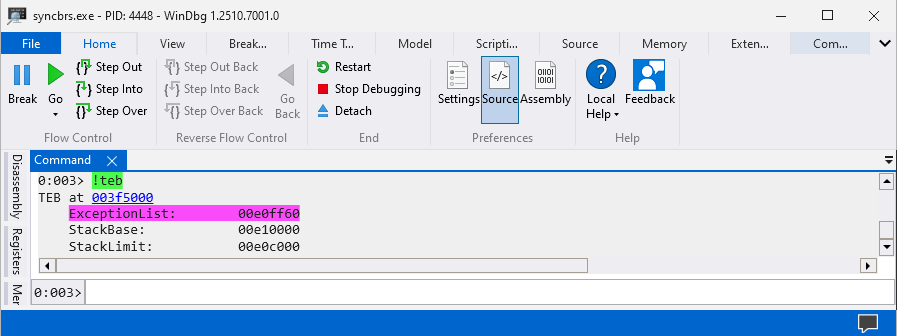
-
Accessing the
_Exception_Registration_Recordstructure using address ofExceptionListpointer.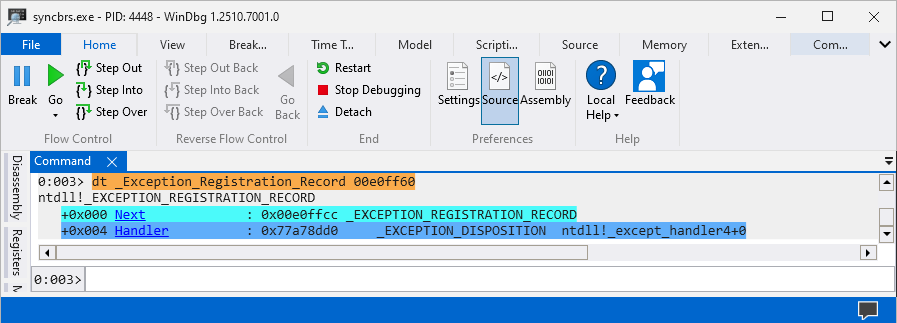
It’s important to note that the pointers Next and Handler plays a crucial role during a SEH overflow as these will be used to epxloit the application. We will go through that in the next section…
Overwriting Handler & Next Pointers
When the payload overwrites addresses within the _Exception_Registration_Record that is a strong indication the application is vulnerable for SEH overflow. Here is a overview of accessing _Exception_Registration_Record after SEH overflow.
-
Getting current exception handler chain.
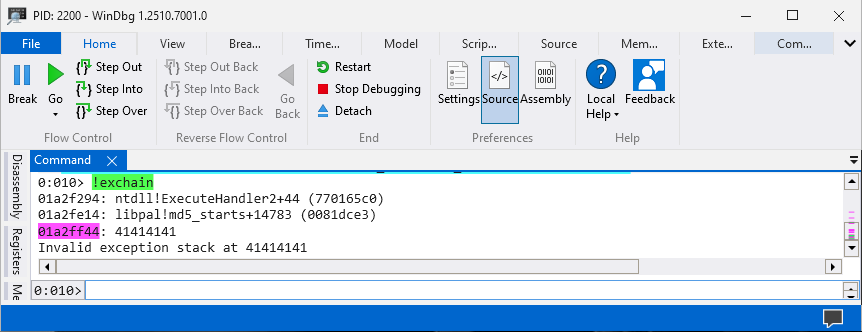
-
Getting
NextandHandlerpointer data.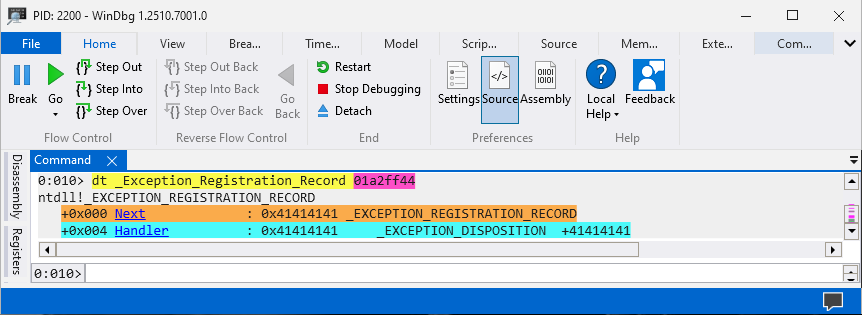
The Handler pointer address will be overwritten with an address that has the POP, POP, RET instructions as that will allow us to jump into the stack. The Next pointer address on the other hand will be replaced with JMP 0x6 instructions to jump over the Handler address once we are inside the stack.
Conclusion
Structured Exception Handler (SEH) is commonly used by developers to act on unexpected events. However, we can exploit it by overwriting the Handler and Next addresses that is inside of Exception_Registration_Record to jump inside the stack and execute our malicious code.
It can be difficult to understand SEH overflow if you’re not familiar with Buffer Overflow therefore I highly recommend reading through the following articles What is Buffer Overflow? and Sync Breeze Enterprise v10.0.28 - Exploit Development Writeup.